

As the cyber threat landscape evolves, cybercrime is becoming more professional, leading to more frequent and sophisticated attacks. All businesses are experiencing increased cyber risk – no one is excluded.
Mergers and acquisitions can cause an even higher period of risk as cybercriminals take advantage of the confusion, disarray, and shift in processes that can reduce an organization’s ability to detect and respond to potential attacks. Since small businesses make up a significant portion of acquisitions, they are a common target for cybercriminals who are looking for opportunities within the acquisition process.
As part of a due diligence assessment, an organization should consider all potential risks that an acquisition poses to an organization, especially cyber risk. Here’s why.
As cybercriminals have honed their techniques, companies face a wider range of cyber threats than before. These cyber threats pose various risks to an organization, including:
If a potential acquisition target has suffered a data breach, or if their current security posture leaves them exposed to cybercriminals, then they’re a less than stellar investment. When evaluating a potential acquisition, investors need to consider whether their potential investment has appropriately managed its cyber risks or the risks may pass on to the investor or acquiring company.
Assessing an organization’s cybersecurity risks can be difficult due to the complexity of the cyber threat landscape and corporate IT environments. When performing due diligence as part of an acquisition, here are some important considerations.
The cyber kill chain describes the various phases that a threat actor moves through when performing an attack.
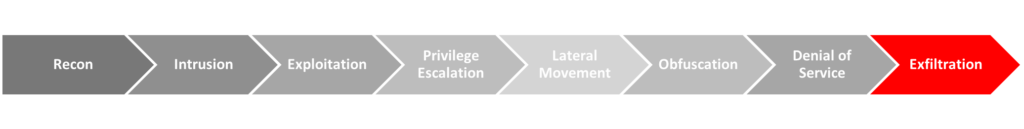
Organizations can detect and respond to potential threats at any point in the kill chain, and the sooner that a threat is identified and managed, the lower the cost and damage to the organization. By using the kill chain as a guiding principle when analyzing a potential acquisition’s defenses, investors can ensure that an oversight doesn’t leave security gaps.
This means assessing its proactive defenses across multiple risk areas.
Prevention is the best and most cost-effective method of managing cyber threats. If an attack can be blocked before it can gain access or do damage to an organization’s systems and data, then the cost to the company is limited.
However, prevention won’t always work, and threats occasionally slip through an organization’s defenses. For this reason, an organization should also have solutions and processes in place to detect and rapidly respond to cyberattacks, including:
The combination of these proactive measures provides user-centric detection and response over network-centric detection, which is more applicable given how attackers are often leveraging social engineering to compromise organizations in the first place. Having these measures in place can help kick out an attacker even after they’ve gained access.
Many cyberattacks target or take advantage of the people within an organization. For example, phishing attacks are some of the most common threats that a company faces. These are attacks designed to trick people into doing something that benefits the attacker.
Security awareness training, phishing protection, and other human-focused security measures should be a part of a potential acquisition’s security program. When assessing a target, having these systems and processes in place vastly reduces the risk of a major attack vector.
Employees should be trained to recognize phishing threats such as Business Email Compromise (BEC) attacks and other social engineering threats.
Companies should also have measures in place to protect their employees and contractors and their online accounts. For example, the use of multifactor authentication (MFA) should be enabled and enforced wherever possible.
Email-borne threats are one of the most common attacks that a business will face. In addition to spam, companies commonly face phishing attacks designed to steal employee credentials or deliver ransomware and other types of malware.
Email protection should be a core part of an organization’s security infrastructure, including the ability to detect and filter malicious content.
A company should also have solutions in place to address threats that slip past the filter, such as deploying an antivirus on all corporate endpoints that can detect and eradicate email-borne malware. This is also where having a comprehensive security posture can build security in layers. Even if a phishing email makes its way past a filter, an organization’s security awareness training can help employees spot the threat.
While endpoint security has always been an important part of a corporate cybersecurity program, its importance has grown with the shift to remote work. Employees working from home may not have the same level of protection as those working from the office.
To manage these threats, a potential acquisition should have endpoint security solutions deployed on all corporate devices, both on-prem and remote. This includes the use of EDR solutions to provide much-needed security visibility and protection of endpoint systems.
An organization should also have security solutions that are capable of managing the most common and high-risk threats that their employees and endpoints face. For example, the emergence of ransomware as a major cyber threat means that companies should have ransomware protection in place for both traditional and double/triple extortion ransomware attacks.
Cyber threat actors rarely immediately gain the privileges and permissions needed to carry out their attacks. For example, a threat actor may initiate the compromise on a user workstation, but an attacker may need access to the corporate database server to maximize the impact of their attack.
Cyber threat actors commonly perform privilege escalation techniques to gain the access they need, moving laterally through the target network and gaining access to the accounts required to achieve their goals. Potential acquisition targets should have solutions in place that can detect attempts at lateral movement. It’s also important to assess their corporate systems – it should be designed based on the principle of least privilege to minimize the potential impacts of a compromised account.
A managed security service provider (MSSP) offers third-party security support to an organization. For companies with undersized or non-existent security teams, an MSSP can provide the security capabilities needed to protect the organization against attacks, including 24/7 monitoring, access to security solutions, and incident response support.
For investors going through due diligence before an acquisition, an MSSP can provide an unbiased assessment of a potential acquisition’s current security posture. An MSSP has the tools, experience, and personnel necessary to efficiently evaluate a company’s potential risks, the maturity of its cybersecurity program, and the steps needed to remediate any identified gaps.
An MSSP also has the ability to immediately uplift a company’s security posture before or during an acquisition to protect their investment. With outsourced cybersecurity, an investor can deploy a mature, resilient security architecture without the time and expense of building a security team in-house.
SolCyber has extensive experience in securing organizations of all sizes and offers consulting services for due diligence for mergers and acquisitions. Learn more about our security offerings for investors.


By subscribing you agree to our Privacy Policy and provide consent to receive updates from our company.






