

When it comes to cybersecurity, companies large and small are up against the same adversaries. While the most advanced hackers would once target only large companies, hackers have started to use the same advanced techniques as part of larger campaigns. In many cases, attacks on SMBs are just as profitable, so that’s what they do.
This, naturally, becomes problematic because small and mid-sized businesses (SMBs) don’t have the same cybersecurity budgets as major corporations. Bank of America, for instance, spends $1B a year on cybersecurity.
So how can SMBs get the same coverage without the price tag? With the minimum effective dose of security.
At first glance, minimum effective dose might sound alarming. After all, isn’t more better? When it comes to protecting your company’s data, not necessarily. There are more than 3,500 security vendors that offer protection at a specific point or points in the kill chain.
Cybersecurity is rapidly changing and those who aren’t immersed in it every day, can’t be as confident in which tools are needed to be cyber resilient. So, they panic and buy more than they need. Worse, sometimes those security tools don’t work well together, and companies are still left with holes in their defense systems.
At the end of the day, you need the ability to stop an attacker from getting in and completing their mission. Securing endpoints alone or barricading your data behind a perimeter wall won’t do the trick. The key to becoming truly resilient against modern threats is to build a tech stack of security defenses that work together seamlessly. When you can achieve this without overpaying for unnecessary protection, you’ve got your minimum effective dose of security.
Your strategy should minimize risk by placing controls at each point in the kill chain (see Figure 1.) which is a framework that defines the different phases of a cyberattack.
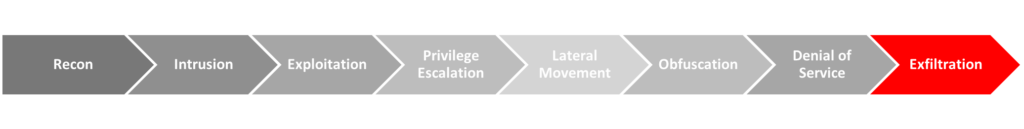
It’s commonly used to build defense strategies and ensure you’re covered with each move an attacker makes. To build an effective strategy centered around the kill chain, you need to:
At SolCyber, we offer this in our Foundational Coverage services. By taking these four elements, we’re able to provide a minimal effective dose of cybersecurity that includes a curated technology stack, 24×7 SOC capabilities and security advisory.
The first step in adopting a resilient security posture is to harden your environment and shrink your attack landscape. This will not only make it harder for hackers to break into your organization, but it will make it more difficult for them to move around once they’re in. The goal is to delay attackers at each step and make it as difficult as possible for them to move laterally across your systems.
When securing your systems, start by patching any vulnerabilities that attackers can exploit. Though patches minimize the risk of a breach, they aren’t always practical, so it’s important to have other controls in place as well, like protecting your active directory (AD). Your AD contains the keys to your kingdom – attackers can get the necessary privileges to access the systems and ultimately the data they’re targeting. So, make sure they can’t gain additional privileges with strong AD policies. You should also carefully control admin access as those privileges can be abused. Minimize their use and remove admin access entirely wherever possible.
Though you ideally won’t have to use them, it’s wise to set up off-site backups. Ransomware attacks are becoming more and more common for SMBs, so having an off-site backup can significantly reduce the time to recovery. Unfortunately, hackers are aware of this, so they often attempt to disable or disrupt the backup process if they can.
Securing your systems is only half the battle when it comes to your attack landscape. The most common way attackers get into SMB systems is through phishing emails that prey on naivety or errors in human judgement. Train your staff to be more alert and make sure they know how to identify even the most convincing phishing emails. Run phishing simulations and break up your cybersecurity training into small, digestible chunks that allow your staff to fully absorb—and retain—the information. How often does your brain turn off when faced with a 60min training video?
A craftsman is only as good as their tools or is it the other way around? Either way, it’s essential to empower your people and environment with technology. With so much choice in the market, it’s often here where costs can explode, and you deviate from the minimum effectiveness dose – who doesn’t want one more shiny new toy?
The technology you choose should maximize your detection capabilities while reducing the amount of time it takes for your analysts to respond and recover. At SolCyber, for instance, we built our Foundational Coverage tech stack using the following principles.
The deeper an attacker crawls into your system, the more damage they can do. We recommend doubling down on security as early in the kill chain as possible. To maximize your chances of detecting an attack before it’s too late, focus on intrusion, exploitation, privilege escalation and lateral movement detection.
Roughly 95 percent of attacks start with a phishing email, so this is a great place to invest. Look for an advanced email solution with multiple detection engines that scan for both phishing techniques and business email compromises.
Once attackers have entered your organization, they’ll land in an endpoint and gain a foothold. Endpoint protection platforms (EPPs) can harden your system and prevent this from happening. Endpoint detection and response (EDR), on the other hand, is the practice of continuously monitoring endpoints and hunting for threats that may have been missed. Both EPP and EDR are essential components to a strong security posture.
As we previously touched on, AD is the primary privilege control in your environment. Having the ability to view and detect malicious requests there is critical to limiting attackers’ ability to move laterally through your system.
Whether you’re managing security in house or have outsourced it to an MSSP, it will be impossible to prevent every attack against your system. The key is to rely on prevention, detection and response in equal measure. Invest in 24×7 monitoring and detection and then respond to any attacks you may have missed.
For every prevention capability there needs to be a corresponding detection capability. As a part of our Foundational Coverage, we prevent privilege escalations by locking down admin accounts and hardening your AD. But if those controls fail, SolCyber can still detect that activity with our EDR solution or Active Directory abuse technology.
Our curated Foundational Coverage tech stack is designed to feed information back into the SolCyber SOC, so we can respond to threats quickly. Our analysts can not only remotely access our clients’ systems to revert any changes made by the attacker, but we learn from those attacks and revise controls to prevent similar attacks in the future.
SolCyber is not your average MSSP. We believe in providing the minimum effective dose of security and Foundational Coverage that just works. We don’t just take over your existing environment, but we bring everything that’s needed to keep you safe. We understand you don’t have the time to assemble a tech stack fast enough to keep up evolving attack strategies.
If you’re interested in getting an enhanced security posture without the bloated tech stack and Fortune 100 price tag, drop us a note and let us know how we can help.


By subscribing you agree to our Privacy Policy and provide consent to receive updates from our company.






